Guest
Guest
Create New Topic As guest or Sign in
Assign topic to the user

-
Information technology and Risk management
In the article mentioned in the subject (https://advisera.com/27001academy/blog/2014/03/31/iso-31000-and-iso-27001-how-are-they-related/), there is an image (see attached).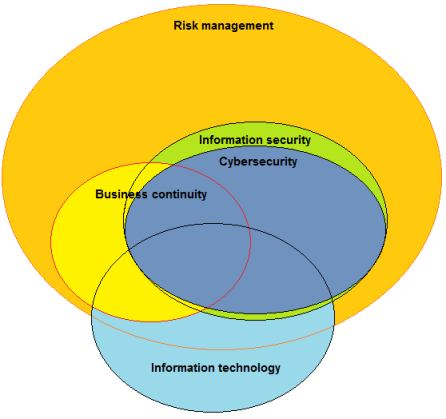 My question is... Why information technology bubble is a little outside form the Risk management bubble?
My question is... Why information technology bubble is a little outside form the Risk management bubble?
-
Information Security in Project Management and Legal aspects
1) Information Security in Project Management - how to implement this -
ISO 27002 certification
As a noc, soc, and general systems engineer ....... would it be beneficial for me to take the Exin ISO 27002 certification exam? -
Becoming ISO 27001 auditor
I have an enquiry about becoming an ISO 27001 auditor. Once I completed the Auditor training course, can I start support doing audits and what rate would I typically expect to work at as a consultant? -
Clauses 4.1 and 4.4
Please let me where I could find the templates related to clause 4.1 and 4.4 -
Structure of the Risk Treatment Plan
Hi friends, I have a doubt about the Risk Treatment Plan, How to structure it? For example, can I to organize the RTP according to risks? controls? assets? o according what? Which columns should have it? and which is the best way to do this document according the ISO? Thank you. -
Quick Risk assessment
I have a document with many questions to check against my software, based in the controls of ISO. The System shall have a logoff button. So, I am compliant or not. If I am not compliant, so I need to do the risk for this item? Using the matrix to calculate. After do it for all items I did the risk assessment? Is it the correct why to do the risk assessment? -
Business Continuity
I have a question, I´m going to work in process for business continuity (A.17.1.x), but I don´t have a clear idea for this process. Do you have any document or some guide that I can use for this part or just for the item A.17.1.2. -
Disaster
a.- Do you have available articles, where you give your advice in how to define a disaster in a DR plan? -
Asset management
Concerning my query on Asset Management

