Guest
Guest
Create New Topic As guest or Sign in
Assign topic to the user

-
Exclusions of the ISMS scope
If a unit in the organization (let us say HR) is excluded from the scope, there is a dependency between HR and other units (for example, HR is responsible for recruitment and training). Although HR is excluded from the scope, it still provides training for employees of other departments that are included in the scope. In this case, HR should be considered an external third-party provider to the other organizational units that are included in the scope, which means that HR should be controlled as a supplier.
What do you think?
-
Creating the Register of Legal, Contractual, and Other Requirements
I'm in the process of creating the Register of Legal, Contractual, and Other Requirements.
Q: how specific do I need to be? Is this where I list all our clients, suppliers, etc etc or do I give more top-line information and detail the specific interested parties later on?
-
TISAX and ISO 27001
I hope this message finds you well. We are in plan to implement TISAX and ISO 27001. we have one IT staff member and there is a confusion on whether he should be sitting by himself in a secure office/area. My CEO requested to ask if the clauses or interpretations in either TISAX or 27001 specifically call for IT staff to have their own office area. Our Current IT staff is sharing the office with a member from purchasing department.
-
Security Awareness Training Records
Is it compulsory to record attendance at this training? Would an ISO 27001 auditor require such a record?
-
Clarification Regarding Control Review Frequency in Policy Documents
I wanted to clarify that all the policy documents we've prepared specify a requirement for a 6-month review. However, the specific controls we discussed are not mentioned in the documents. My question is whether, according to the policy, we need to review the controls every 6 months or if we have the flexibility to define the update frequency for the controls ourselves, separate from the document reviews. Please refer to the attached image for more details.
-
Risk levels and decision-makers
About risk levels and decision-makers, could you share some insights? I got confused on who will be the decision maker on putting the level of the risk and based on which criteria the level was set?
-
ISO 27001 Internal Auditor Course Question
In Module 7 Audit Findings, the quiz asks to the student to select which finding is an observation with the correct answer nominated as “The procedure for internal audit can be improved by adding an audit plan”. I would argue that this is a non-conformity as ISO27001-2022 cl 9.2.2 requires the organisation to plan, establish, implement and maintain an audit programme(s), including the frequency, methods, responsibilities, planning requirements and reporting. If an audit plan is not available at the time of the audit, is this an matter of noncompliance with the part of the standard?
I’d appreciate your thoughts and any clarification that you might be able to provide.
-
Certification scope
As we have two entities, one in Site A operating under the supervision of the regulator and 2nd in Site B providing services for the Site A entity, a few things to clarify:
- Is the setup, documents, actions etc. enough for both entities, or I will have to prepare two different setups?
- Also do we have to pass an audit to certify both entities or only the regulated body is enough?
In addition to that, the situation now is slightly changed as we have another regulated entity in Site C and I need this to be added in the answer. I need clarification on how to action as we have now in total 3 companies under Company:
Company A - the Site B company that is providing services for the rest of the companies
Company B - the Site A-regulated company
Company C - the Site C-regulated company
-
Security Awareness Course Password Question
One of your questions/answers (
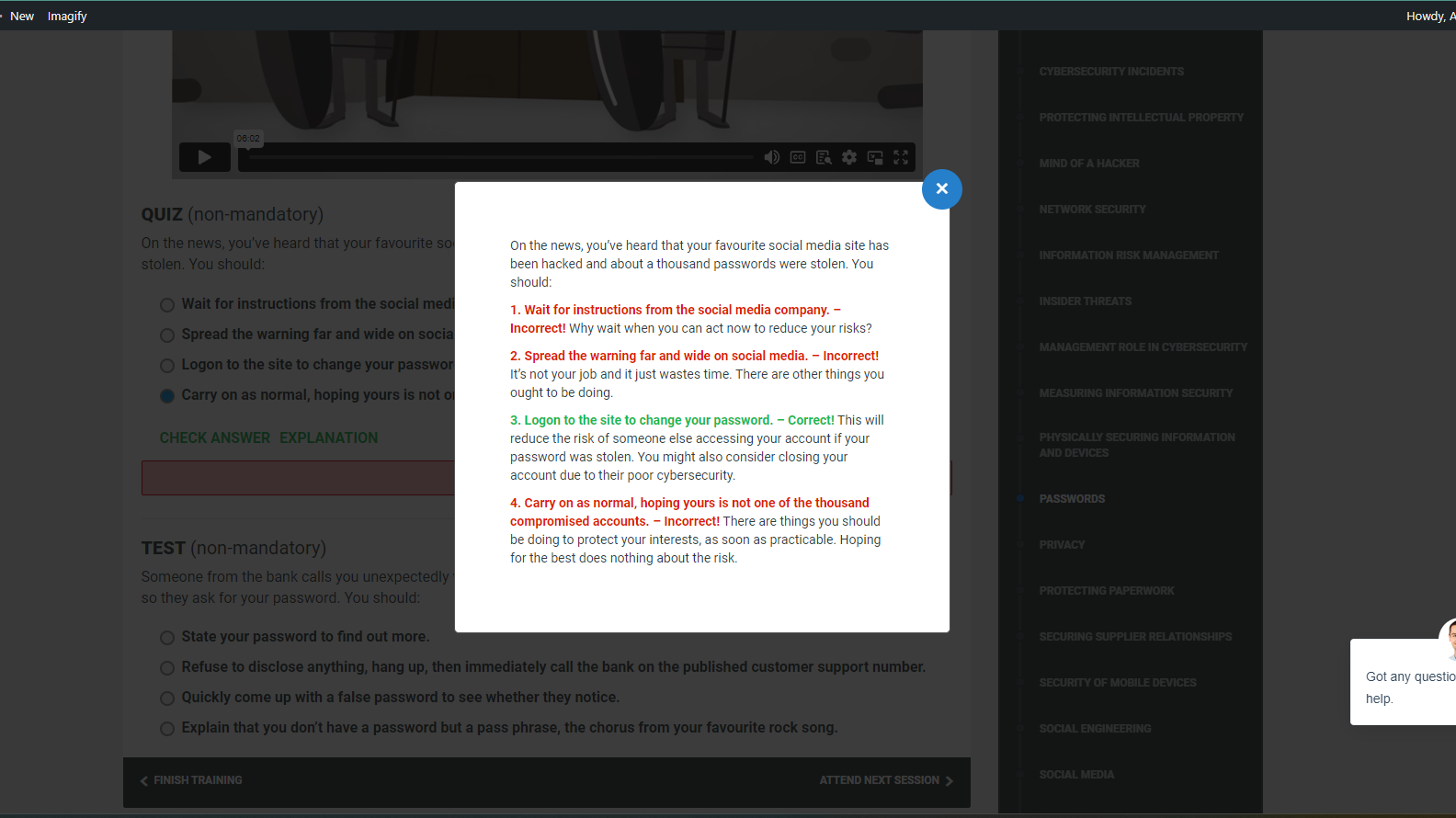 ) is incorrect according to typical security best practices. If the security of a website has been compromised, you should absolutely not long in immediately if they have not told you to. While you might consider changing passwords on any other site where you've used the same one, logging in and updating it on a site that may still have an incident in progress only increases your risk."
) is incorrect according to typical security best practices. If the security of a website has been compromised, you should absolutely not long in immediately if they have not told you to. While you might consider changing passwords on any other site where you've used the same one, logging in and updating it on a site that may still have an incident in progress only increases your risk."
